In this CTF, I just only can solved Rev - MoM's Touch.
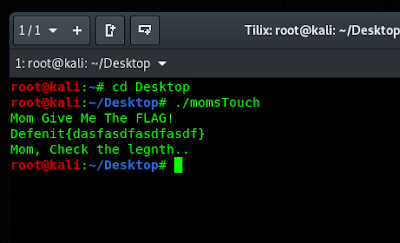
Description: My mom wants me to bring a flag.. Please get my flag back to me!
- As usual, use Exeinfope to find the format.
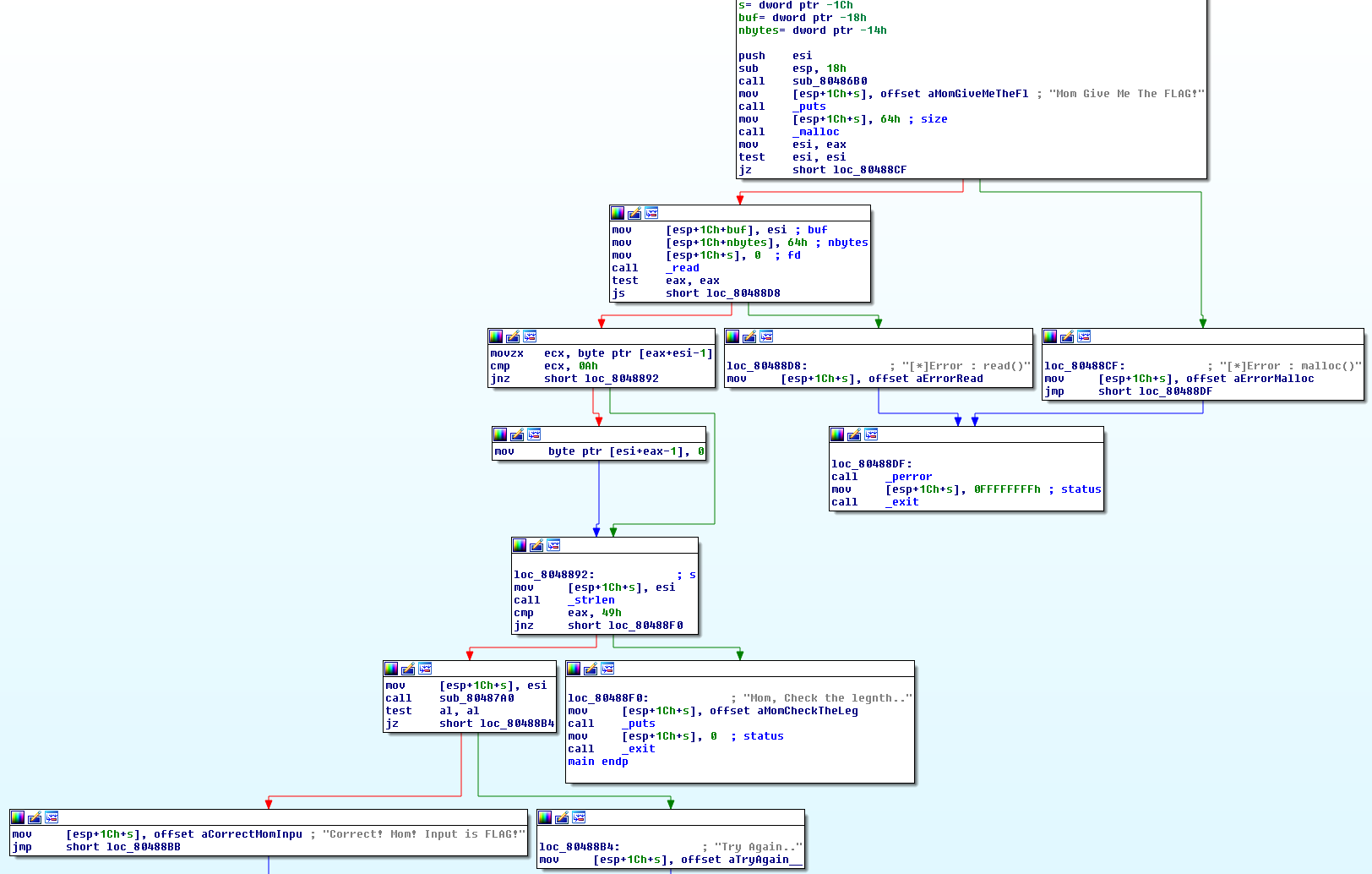
- Next, I ran it in Linux for preview and then put it in to IDA, started to reading it.
- As I saw, if the length equal to 0x49, script will call sub_80487A0 and check the flag.
- Press F5 in sub_80487A0, I had pseudo-code.
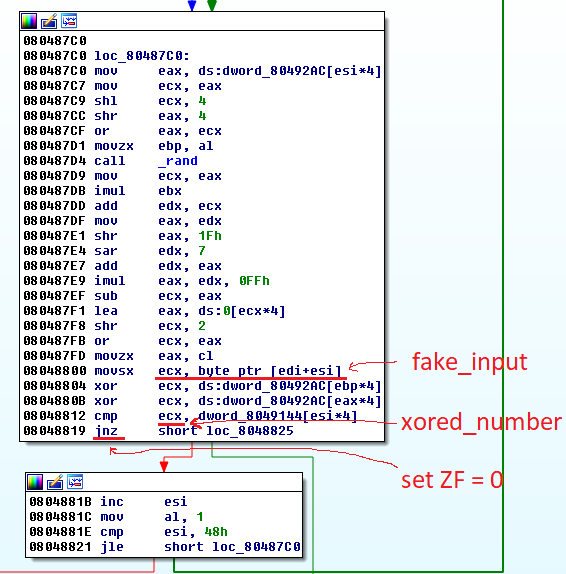
- In short, sub will get rand() as v3, something at dword_80492AC[calculate base on v3] and dword_80492AC[swap bit of v1 (v1 is the order)].
- And then, we have the comparison of
- dword_80492AC is hidden, dword_8049144[v1] is public. Easily, I knew that I could get inp[v1] if I xor the other 3 variables.
- To do that, I used library gdb for python in oder to:
- First, send fake_input.
- Second, I used the xored_number xor with fake_input in order to get dword_80492AC[calculate base on v3] ^ dword_80492AC[swap bit of v1].
- Then, I can xor with dword_8049144 and get the true_flag.
- Finally, set ZF = 0 in order to continue the for loop.
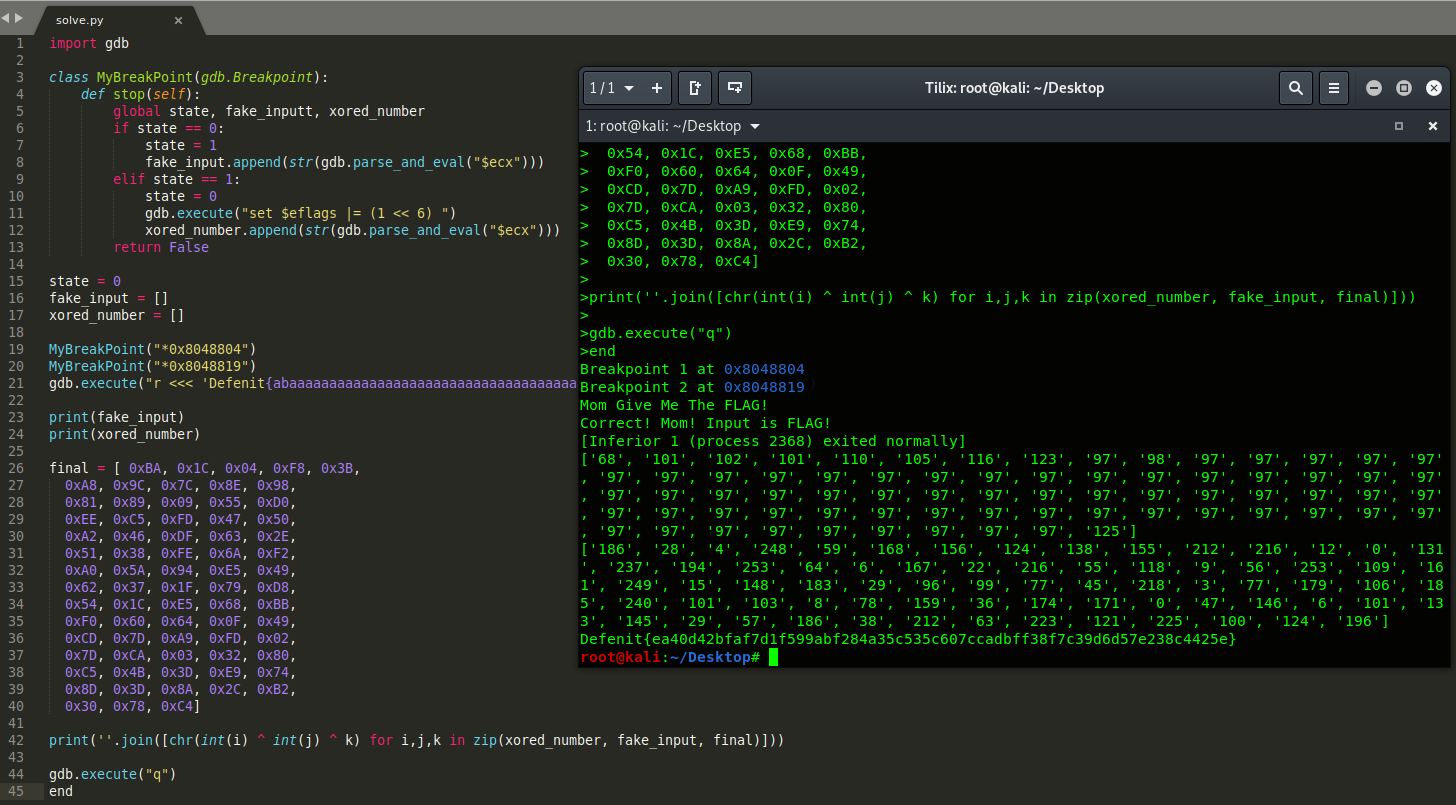
- This is the result.
 |
| set breakpoint at 0x8048804 to get ecx (fake_input) after defined at 0x8048800 set breakpoint at 0x8048819 to get ecx (xored_number) and set ZF = 0 |
- The code: solve.py
- Addition. In order to run the code, open terminal and type < gdb ./momsTouch > to start gdb debugger. Then, type python and paste the code, enter.






No comments:
Post a Comment
Sending successfully