- In this contest, I had solved 6 (1 unofficial) challenges.
AP Lab English Language
| script |
- This challenge gave us a script that done something like swap index of characters of the input. After that, if input is equal to "1dd3|y_3tttb5g`q]^dhn3j" , the input is correct.
- For the algorithms, transpose function choose new character for each character in "ret" base on "input" and "transpose". Then, all characters xor with numbers corresponding. Do it for three times.
- For example,
- input = "abcxyz"
- transpose = {4, 2, 3, 1, 0, 5}
- Then, ret = "ycxbaz"
- For the solution, if I have "ret" string, I can get the previous string.
- There are two ways to solve.
AP Lab Computer Science Principles
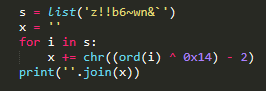
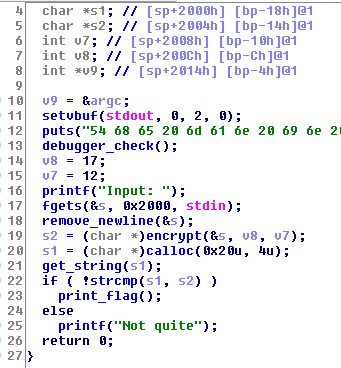
- This challenge requests "input", decreases each char with its order and plus with the length of the character as decimal number on ascii table.
- For the solution, with each order, I try all possible printable char and do exactly the action of source code.
| script |
dis
- I received a disassembly of python code named "disas".
| script |
- Depend on some documents on the Internet, I knew how the disassembly code show out.
-
In short:
- LOAD_FAST: local variable.
- LOAD_GLOBAL: global variable, function.
- LOAD_CONST: number.
- FOR_ITER 24 (to 48): for loop from line 24 to line 48.
- CALL_FUNCTION n: call the function was LOAD_GLOBAL in n+1 previous line. Arguments are n nearest line.
- This is original python code after rewrite.
| script |
- This is solution when I reversed all calculation.
| script |
Ice Cream Bytes
- This challenge gave me 2 file: IceCreamBytes.java and IceCreamManual.txt.
- In short:
- First, java file read and collect some characters from IceCreamManual.txt in function fillMachine().
- Second, input run through numbers of function and compare with previous string which returned from function fillMachine().
-
For the solution, we need reverse the processing:
- toppings(chocolateShuffle(vanillaShuffle(strawberryShuffle(input))))
-
To this:
- strawberryShuffle(vanillaShuffle(chocolateShuffle(toppings(string))))
- Also, all calculations in those functions must be reversed.
- Here is the script.
Recursion Reverse
- This challenge gave me Ascii.java
-
For the algorithms, script get the input and then put it into flagTransformed().
-
Each character plus with pickNum( its_index (or i) ):
- Calculate sum of first i number.
- If it is even then return the num else continue call new function.
-
Note:
- When order equal to 11, num will very very big and if we use for loop, time is very slowly. To deal with it, I replaced it with O(1) calculation.
- The type of num is int32, that means I have to use numpy.uint32 in order to convert num to int32 number before return.
-
As usual, for the solution, I try all printable character on each index, calculate and compare with the given string.
| script |
AP Lab 3D Design (unofficial)
- This challenge gave me a file named AP3DDesign.class. In order to read code, I use this website to decompile class file to java file. AP3DDesign.java
- In short,
- Input receives 25 character, then splits into 5x5 matrix, each of them are converted to 8 bit binary. As a result, we have 5x5x8 matrix.
- Next, for each order in binary number, function shuffle1() will swap the corresponding binary bit in each element of that row together.
- Finally, shufle2() will xor the corresponding element.
- For the solution, I just xor and re-swap with the correct position.
- This is my script.
- Because of some reasons, author did not upload the challenge again, so that I could not test my solution. Perhaps it is right.