I played this ctf at ZombieBot team and only solve 4,5/11 easy RE challenge
Cracker Barrel
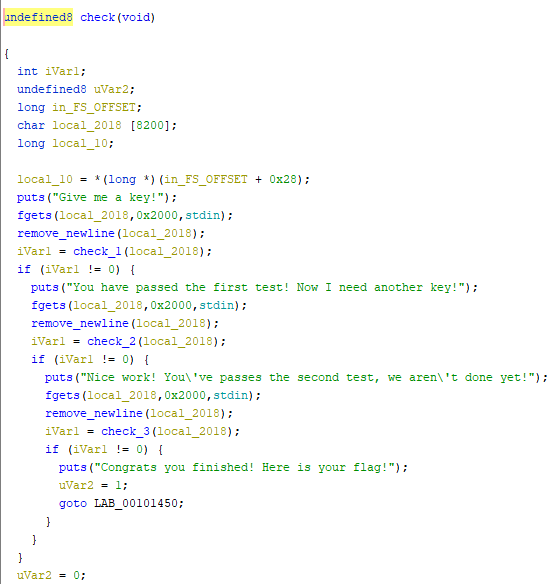
- Using Ghidra, I saw this:
- 3 input for check_1, check_2, check_3. Receive true for each check.
- Input must be "starwars" in order to set uVar2 = 1 = True
- Reverse the input 2 must equal to "si siht egassem terces" -> "secret message this is"
- For each pvVar2[i * 4] = (input[i] + 2) ^ 0x14. Then, pvVar2 = local_48. local_48 = [z...!...!...b...6...~...w...n...&...`]
- input 3 = l33t hax0r
Mr. Game and Watch
- Again, I had 3 input for crack_1, crack_2, crack_3.
- Crack_1:
- MD5(input) == d5c67e2fc5f5f155dff8da4bdc914f41
- decrypt online = input = "masterchief"
- Crack_2
- SHA1(input) == decrypt(secret_2, key_2)
- decrypt():
- return += secret_2[i] ^ key_2
- SHA1_decrypt(return) = input = "princesspeach"
- Crack_3
- encrypt(sha-256(input) , key_3) == sec_3
- sha-256(inp) = de_encrypt(sec_3 , key_3)
- encrypt():
- return += input[i] ^ key_3
- sha-256_decrypt(return) = input = "solidsnake"
Sora
- Using Ghidra, I found the function encrypt()
- Open with IDA, I saw this:
- It is a simple script that encrypt(input), save into s2, and compare with something from get_string(), save into s1.
- Look into encrypt()
- get_string()
- Using shift + E to export data and get the given string.
- For encrypt() function, like previous chall, if we send a character, we receive another character and compare with given string. But the algoritms is seem to be different from assembly code.
- This challenge have 2 ways to solve.
- First, send all possible character and find out the previous version of given string.
- Note: This challenge have debugger_check() in order to prevent player. Wanna by pass, just set breakpoint at following address and set ecx = 1.
Chestburster
- This challenge did not have decriptions, just given an exe.
- Open with IDA, I saw
- sub_2E1120() had a long process that, in short, change a position of the input and compare with "welcome_to_the_jungle!"
- For this chall, I just simple wrote down the algo and reverse the role of input and output.
- Script
- input = "lmo_ewce_j!eo_tulgneht"
- When I write it into server, it led me to port 30009 and "question.php".
- Unfortunately, I can not find the rest of this challenge.
- You can read the rest of this challenge solution on this, from Archercreat. He is very great!


























No comments:
Post a Comment
Sending successfully